Access Management for cloud resources is a significant function for cloud using organization. Azure Role Based access control (Azure RBAC) assists in managing the actions of one who has access to Azure resources and also which segments they have access.
Azure RBAC is an authorization system built based on Azure Resource Manager (ARM) which provides throughout access for relevant resources.
Use Cases of implementing Azure RBAC:
- It allows one user to manage VMs and another to manage networks at the same time simultaneously
- SQL database can be managed by DBA group
- Also allows one single user to manage all resources in a group, like virtual machine, websites and subnets
- All resources in a resource group can be accessed by a single application
How it Works
The key principle of how RBAC works and controlling the access to various resources is creating role assignments and how permissions are enforced. The method of assigning roles consist of three elements: security principal, role definition and scope
● Security Principal:
An object which comprises of four segments- user, group, service principal, or managed entity
● Role Definition:
It is stated as cluster of permissions. It lists the variety of operations to be performed which includes read, write and delete.
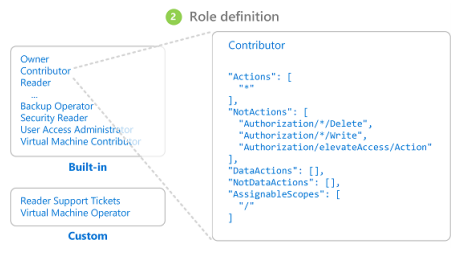
Several built in roles that Azure includes are as follows:
- Owner- Can be called as the parent as it has access to all resources
- Contributor- Has access to creating and managing all Azure resources
- Read- Viewing the existing resources
- User Admin- Lets us manage user access to all Azure resources
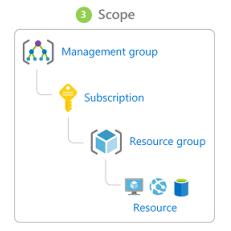
Scope
Scope is a set of resources that limits further actions while assigning roles that is, it applies if you allow to make someone a website contributor but for a single resource group
Role Assignments
It is a process of confiscating role definition to a user, group, service principal or managed identity for the intention of granting access. Marketing users don’t have access to resources outside, until they are a part of another specific role assignment.
Steps to Determine Whether User has Access to resource
Following are few significant checkpoints to make understand when troubleshoot an issue:
- User acquires a token which includes group memberships
- User makes API call to resource manager with the attached token.
- All the role assignments applied to resource are retrieved by Azure resource manager.
- Role Assignments applied to the user or the group gets restricted by Resource Manager
- It determines whether if the action in the API call is included in the roles in respect to the user
- Access gets blocked in any denial of assignment comes into play
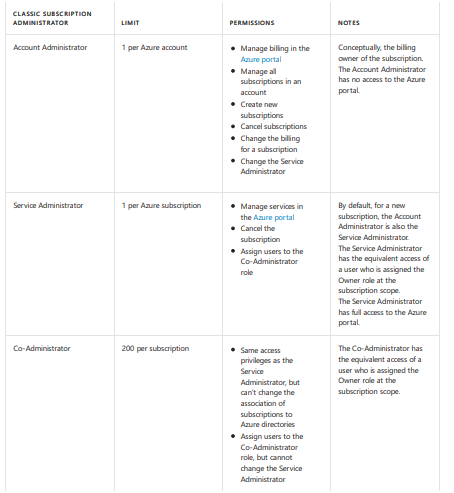
Classic Subscription Admin Roles
There are three classic subscription admin roles-Account Admin, service admin and co-admin. They use the Azure portal, azure resource manager and classic deployment model APIs to manage resources. The service admin and co administrators both have equivalent access of users who have been assigned an azure role. Below are the differences between all three classic admin roles:
Azure Subscriptions
Azure account is basically a user identity, multiple Azure subscriptions and set of Azure resources. The account admin is the person who creates account for all relevant subscriptions which later assists in compiling and manage all access and billing for resource usage. All subscriptions directories are can be found in Azure portal associated with open subscriptions in Azure portal.
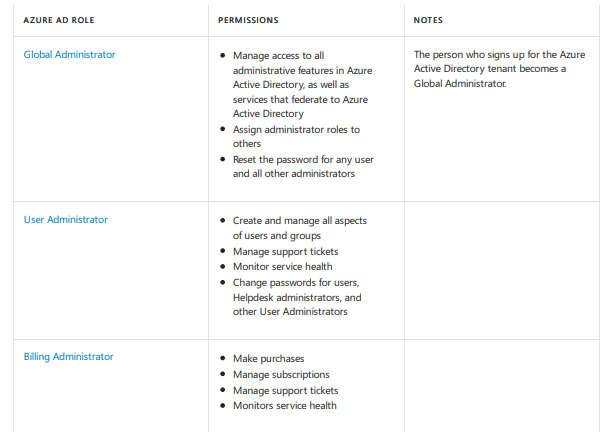
Azure AD Roles:
All create or edit and delete users, reset and setting passwords, user licenses are stated in a directory related to Azure AD resources which are managed by AD roles.
Description of Roles:
Viewing Role Assignments
Following steps are mentioned below to view role assignments
- User will log into Azure portal and then click on All services and Subscriptions
- User will select an individual subscription
- Have to select Access Control(IAM)
- Then user will have to click the check access
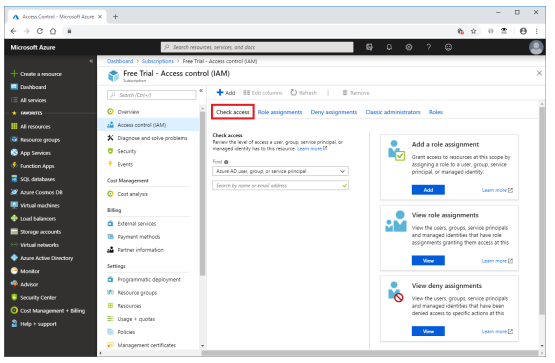
- Under the Find List, the respective type of security principal should be selected which the user wants to access.
- A search box appears in which, user will have to enter a particular string for display names, email address or object identifiers
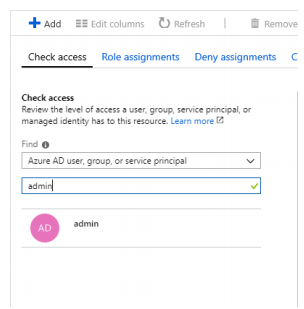
- Security Principal will be clicked to open assignments pane
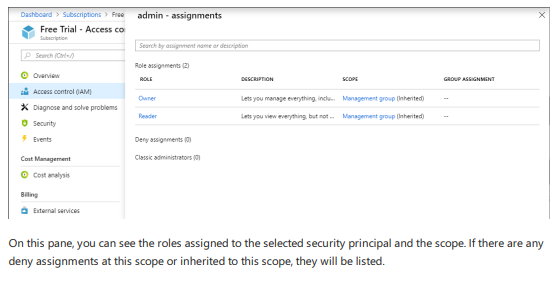
In this pane, user will be able to view the roles assigned to the selected security principal and scope.



